Android trackers and permissions: Did I say you could do that?
June 15, 2020 / Alex LintonPrivate messaging
As netizens have become more and more tech-literate over the years, lots of people have developed their own list of ‘scam app’ red flags to look out for. This might be things as simple as poor reviews, poorly written app descriptions, or things just looking plain dodgy. Most people have been around the internet rodeo for a while, and they can smell spyware from a million miles away.
But when you’re not quite sure — when some things seem right and other things don’t — you need cold hard facts to help you out. For a lot of people, the permissions required by an app is one of the first things to check out.
You shall not…have permission!
Permissions are a big deal in the mobile world, they can give apps the right to access your Android phone’s hardware (like the camera) or personal information (like your geographical location). And apps aren’t like kindergarteners asking their teacher if they can go to the bathroom — a lot of the time, apps are given permissions without explicitly asking.
More serious permissions (like location data) will normally require you to give it the manual tick-of-approval, but if the app is asking for permissions that aren’t directly explained by its functionality, your scam senses should be tingling.
Remember, the size of the permissions list doesn’t necessarily matter: some apps might require a lot of permissions, but there might be legitimate reasons they’re asking for them.
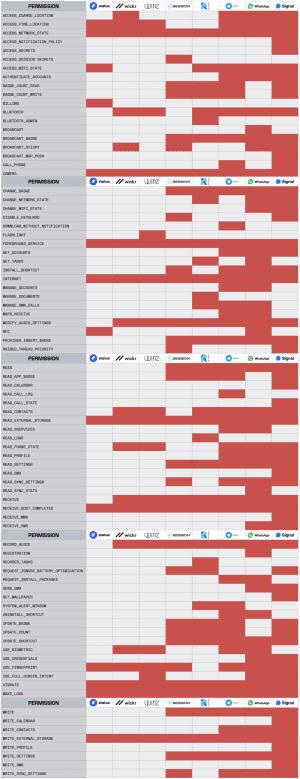
Let’s take a look at some of the best private messengers in the world, and see what kinds of permissions they’re asking for on Android — and why.
Signal has one of the cleanest records going when it comes to security. It’s trusted by tech-heads all around the world, including people like Edward Snowden and Twitter’s Jack Dorsey.
Signal, Telegram, and WhatsApp — the three most popular encrypted messaging apps — require the most permissions. And Signal requires the most permissions of any of these apps — what’s up with that?
Well, it’s not ideal, but it’s probably not as big of a deal as it seems.
A lot of the permissions Signal asks for make sense, like the ability to send SMS messages — because Signal can be used to send an SMS.
Most of these apps — including Signal, Telegram, and WhatsApp — request the ability to view your contacts, probably so that they can check which numbers in your phone’s contacts list are also registered on their app, and suggest you message them. Let’s be honest, that’s really not ideal from a privacy perspective — but at least it’s easy to explain why the permission is needed.
But what about Session? We know all the inner workings of Session, so let’s take a deeper dive into some of the permissions used by Session and why they’re required.
Session permissions on Android: What and why
ACCESS_NETWORK_STATE This allows Session to check whether your device has a valid internet connection, which is required for basic message sending functionality.
ACCESS_SESSION_SECRETS This allows Session to cache information about your encryption sessions for improved performance.
BADGE_COUNT_READ, BADGE_COUNT_WRITE, BROADCAST_BADGE, CHANGE_BADGE, PROVIDER_INSERT_BADGE, READ, READ_APP_BADGE, UPDATE_BADGE, UPDATE_COUNT, UPDATE_SHORTCUT, WRITE These permissions allow Session to manage notification badges for unread notifications.
BROADCAST_STICKY Allows Session to display sticky notifications — notifications that don’t go away after they’ve been seen.
CAMERA Session requires this in order to let you take and send photos in your messages.
DISABLE_KEYGUARD This permission is required in order to enable Session’s PIN lock feature.
FOREGROUND_SERVICE Allows Session to use ‘Service.startForeground’.
INSTALL_SHORTCUT This allows you to add Session shortcuts to your launcher.
INTERNET Allows Session to open network sockets.
MODIFY_AUDIO_SETTINGS This is required in order to set your Session notification sound from within the app.
RAISED_THREAD_PRIORITY This is required to enable certain features that require high processing priority, such as real-time audio playback.
READ_EXTERNAL_STORAGE This is required in order for you to access pictures and files from within Session.
RECEIVE Session uses this to receive notifications from Google Firebase if you have opted in to Google Firebase notifications.
RECEIVE_BOOT_COMPLETED Allows Session to receive the ‘Intent.ACTION_BOOT_COMPLETED’ message which is broadcast once your device has finished the boot process.
RECORD_AUDIO Session uses this for recording and sending voice messages.
REQUEST_IGNORE_BATTERY_OPTIMIZATIONS This permission is used on devices without Play Services installed; Session will prompt the user to disable battery optimizations so the app can poll for notifications in the background.
VIBRATE This allows Session to provide haptic feedback using the device’s vibrator motor.
WAKE_LOCK Allows using PowerManager WakeLocks to keep the processor from sleeping or the screen from dimming when you’re using Session.
WRITE_EXTERNAL_STORAGE This allows Session to save photos and other attachments to your device.
READ_SETTINGS, WRITE_SETTINGS Allows Session to read or write the system settings, such as your notification sound for Session messages.
READ_SYNC_SETTINGS, WRITE_SYNC_SETTINGS Allows Session applications to communicate with devices which use Android sync, such as wearables and Android Auto.
These aren’t the trackers you’re looking for
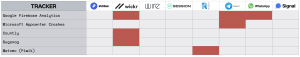
We’re not gonna beat around the bush with this one — trackers are bad news for your privacy, and really you should be looking for apps using zero trackers.
Generally, trackers indicate developers are using some kind of analytics service to see the way you use the app or your device. This isn’t harmless information, and with things like fingerprinting, this could potentially lead to you being profiled or identified by the developer or the analytics services they’re using.
Google is the king of analytics. You’ll see either Google Analytics or Google Firebase Analytics used in Telegram, WhatsApp, Riot, and Wickr — it provides information about 500 unique actions you might perform when you’re using the app. Of course, this information can prove invaluable for developers — but it’s important to make sure it’s always opt-in.
App versions analysed: Status v1.3.0, Wickr v5.54.7, Wire v3.49.921, Session v1.2.3, Riot v0.9.12, Telegram v6.2.0, WhatsApp v2.20.189, Signal v4.63.2
Riot also uses Matomo, which is an open-source alternative. That’s a good step up from giving all your information to Google, but really, we’d rather see Riot find a way to get by without the use of trackers.
Session, Status, Wire, and Signal come up trumps here with no trackers in sight.
Do your own research
Like we said, it’s not really about the amount of permissions required, so much as it’s about what permissions are required. Have a look at some of your own most-used apps and make the call for yourself.
You can use tools like Exodus Privacy to audit your own applications and weigh up the pros and cons of whether it’s worth using for you. As per usual, it all depends on your threat model: something that’s a deal breaker for Alice might be perfectly fine for Bob.
Session Pro Beta update: December 2025
December 07, 2025 / Session
Session Protocol V2: PFS, Post-Quantum and the Future of Private Messaging
December 01, 2025 / Session
Removing screenshot alerts from Session
November 09, 2025 / Session
Session Pro Beta Development Update: Progress and Community Insights
October 30, 2025 / Session
Session Pro Beta: September Development Update
September 23, 2025 / Alex Linton
What to do if you can’t connect to Session in your region
August 14, 2025 / Session