Onion routing: Private messaging’s missing link
December 26, 2019 / Alex LintonPrivate messaging, Security
End-to-end encrypted messaging apps are popping up left and right, but finding the most private and the most secure can feel like a game of Whack-a-Mole — with your online privacy at stake.
Every private messaging app has its pros and cons, but there’s a crucial ingredient missing from their security salads: onion routing.
End-to-end encryption
The gold standard — with a glaring flaw
Traditional end-to-end encryption schemes (like those used by Signal and WhatsApp) are highly secure, and prevent anyone from snooping on the contents of messages being sent over the internet.
But traditional encryption has a pretty big weakness: Hackers might not be able to read messages in transit, but they can still tell who’s talking with whom.
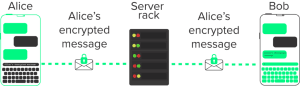
Let’s say we have two people, Alice and Bob, talking to each other using an end-to-end encrypted messaging app. Every message Alice sends to Bob (and vice versa) is wrapped in a secure layer of encryption from the moment it leaves Alice’s phone to the moment it arrives on Bob’s.
If someone else — let’s call her Eve — is able to intercept a message in transit, all Eve sees is a garbled mess of encrypted data. Great!
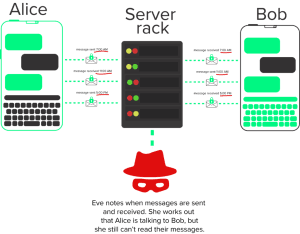
The problem is that even with end-to-end encryption enabled, an observer can still see some information about Alice and Bob. Depending on who Eve is, she can figure out that Alice is messaging Bob by snooping on the traffic moving through the network. Eve could use temporal analysis to identify that since Alice’s phone is sending messages, and Bob’s phone is receiving messages a few moments later, Alice is probably messaging Bob. Eve could also figure this out by gaining direct access to the messaging app’s central server, which would let her see every conversation being conducted using the app.
This is because while end-to-end encryption protects messages in transit, it does nothing to stop someone from discovering who is talking to whom.
Imagine if you were trying to have a private phone call with your partner, but every time you picked up the phone, someone on the other side of the world could figure out you two were talking with just a few keystrokes. Sure, nobody knows exactly what you two are saying — but that’s still not very private, right?
Onion routing
Salad-powered security
Onion routing is a technique for sending data anonymously over a network. Unlike traditional encryption schemes, onion routing doesn’t just stop someone from reading or intercepting data. By using multiple layers of encryption and bouncing messages through multiple servers before they reach their destination, onion routing stops observers from being able to tell who’s talking (i.e. sending data) to whom.
So how does that work, then?
Let’s go back to Alice and Bob. Imagine Alice wants to send Bob a message, but she doesn’t want Eve to know that she’s messaging Bob at all. Instead of opening Signal or WhatsApp, Alice fires up an onion-routing enabled messaging app like Session.
Alice fires off her message:
>Imagine if Eve knew we were planning her surprise party right now!?
When Alice hits send, the Session app encrypts her message twice, then passes the message to Lokinet, which encrypts it 4 additional times (Wondering why 4? We’ll come back to this later). Each layer of encryption is wrapped on top of the others, forming an ‘onion’ of encryption layers, with the message at the centre.
This ‘onion’ message is then sent to a Loki Service Node. This node decrypts one layer of encryption, then passes the message to another service node, which decrypts another layer — this process is repeated 4 times, once for each layer of encryption applied to the message after it left Alice’s Session app. Finally, when the message arrives on Bob’s device, Bob’s Session app decrypts the final two layers of encryption, and Bob reads the message.
The really cool part? Each service node involved in this message-passing chain only knows about the service node it received the message from, and the node it passed the message to. The first node in the chain knows that Alice sent a message, and the last node knows that Bob received a message. But no service node in the chain (and no outside observer) is able to connect the dots and figure out that Alice is messaging Bob.
Onion routing isn’t a perfect solution; an attacker could theoretically use temporal analysis to link Alice and Bob together. However, onion routing — especially when used in combination with a decentralised network structure — makes this type of attack significantly more difficult.
Level up!
Most modern messaging apps offer at least some kind of encryption, and the more secure options, like Signal, are end-to-end encrypted by default. But all this encryption doesn’t really keep your communications private when someone else can still tell who (and when) you’re messaging!
Onion routing gives your private conversations a whole new level of security.
Using an onion routing-enabled private messaging app, you can DM and DnM to your heart’s content — confident that no snooping spectators are watching.
TL;DR:
End-to-end encryption is great for communicating securely, but even if you’re using it, an attacker can still tell who’s talking to whom — even if they can’t see what’s being said. Onion routing protocols, like the one Session uses, encrypt your messages multiple times and bounce them between several servers before they reach their destination. This stops attackers from knowing who you’re talking to, as well as what you’re saying!
Rotating keys for Session repos
January 22, 2026 / Session
Session Pro Beta update: December 2025
December 07, 2025 / Session
Session Protocol V2: PFS, Post-Quantum and the Future of Private Messaging
December 01, 2025 / Session
Removing screenshot alerts from Session
November 09, 2025 / Session
Session Pro Beta Development Update: Progress and Community Insights
October 30, 2025 / Session
Session Pro Beta: September Development Update
September 23, 2025 / Alex Linton