Sim Swapping attacks: How to protect yourself from this common phone scam
September 05, 2022 / Wesley SukhPrivacy, Security
SIM Swapping, the renaissance of scamming.
With more essential services relying on phone numbers as a security method, it's no wonder SIM swapping attacks have surged over the last few years. This growing dependence on phone numbers for verification means tying your identity to your mobile number might not be such a great idea. Let’s explore what SIM swapping is, how it happens, and most importantly, how you can protect yourself from this increasingly common scam.
What is SIM Swapping?
In simple terms, a SIM swapping attack involves a hacker transferring (or “swapping”) your phone number to a blank SIM card in their possession. Once they've successfully hijacked your number, they can access sensitive personal data, often using it to breach your online accounts.
Data leaks, server hacking, organisational corruption, a jealous ex (hey, it happens) or the ever present risk of phishing—the personal data needed for a successful SIM swapping attack can originate from a range of sources. To gain access to your number, scammers will typically impersonate their victim and contact a telecommunications company claiming they need to port the victim's phone number onto a new blank SIM. These (not so) lovely people will use any of the mentioned methods of hacking to convince these employees that their credentials are legitimate. You lose access to your number and the security your number provides.
SIM Swapping isn't necessarily a new form of digital scamming, but it's one that is on the rise thanks to the increasing reliance on two-factor-authentication (2FA). Whilst 2FA sets a strong foundation of protection against password hacking or server breaching, security practices which rely on phone number authentication also open the door for some scary consequences. Which means you have to ask...
What happens to my accounts if someone gets access to or obtains my phone number?
Once a hacker or scammer has ported your number, there's not much they can't access. Thanks to 2FA, a scammer is granted access to (you ready for this?):
Temporary passwords, account resets, the withdrawal of personal funds (usually crypto or other uninsured assets rip), personal identifiers and private data, BNPL (such as Afterpay), Paypal... it can all potentially be targeted.
While the concept of SIM Swapping may not sound as scary as a traditional data hack, it is without a doubt some pretty gnarly identity theft, and we're seeing it happen to both regular folks and tech heads alike. In the states alone, the Wall Street Journal reported that in 2021 SIM Swapping resulted in the private loss of $68 million USD, a figure 5 times larger than the combined 3 years prior. As our dependency on our phones increases, the risk of identity theft continues to grow as our phone numbers become an ever increasing part of our identities. The level of exposure is pretty dangerous when you consider just how many of your personal accounts can be reset from one handheld device.
Vice and other news outlets often run news pieces on the effect of SIM Swapping, showing how unsuspecting victims end up losing years worth of savings. These scams aren't just affecting ordinary people though, in 2019, Former CEO and co-founder of twitter, Jack Dorsey's personal phone number was tied to Twitter's text to tweet service. An alleged security oversight from the network provider allowed scammers to gain temporary control over Dorsey's twitter account (which currently has 6.4 million followers).
How do I know if I've been SIM swapped?
If you notice that you're unable to access your normal range of services, it is recommended you quickly investigate your account status. Be on the lookout for transactions you don't remember making. You should receive email confirmation for most account changes so be wary of legitimate communications from your provider. Early detection allows you to act before you get locked out of any of your accounts.
How can I prevent SIM Swapping attacks?
There are a few simple steps that can help you protect against SIM swapping attacks—and reduce the risk of becoming a victim.
Phishing is a common tactic used by attackers—think of those sketchy emails you warn your grandparents about. Unfortunately, these attacks are becoming more sophisticated. Even if an email seems harmless, it's always better to err on the side of caution. If you're unsure about its authenticity, don’t click any links or provide sensitive information.
Next, safeguard your accounts by using strong security PINs—and avoid reusing the same one across multiple accounts. Also, rethink your security questions—choose answers that aren't easily guessed, like avoiding common information such as maiden names. Lastly, opt for app-based two-factor authentication (2FA) instead of SMS-based 2FA. This makes it harder for attackers to bypass your defenses.
While these steps might take a little extra effort upfront, they will save you far more time and stress in the long run, especially compared to recovering a compromised account.
Use tools like Session to lower your attack surface area.
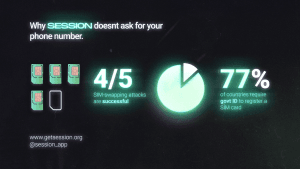
Session was designed to tackle the growing threat of SIM swapping attacks. Since Session doesn’t require a phone number, scammers can't exploit this vulnerability to gain access to your account. You’ll never have a phone number tied to your Session account, meaning there’s one less weak point for attackers to target.
By diversifying your communication methods and using apps like Session, you minimise the potential points of attack and reduce the risk of sensitive data being stolen or exposed. With 4 out of 5 SIM-swapping attacks proving successful, safeguarding important parts of your life by using more secure apps just makes sense.
Rotating keys for Session repos
January 22, 2026 / Session
Session Pro Beta update: December 2025
December 07, 2025 / Session
Session Protocol V2: PFS, Post-Quantum and the Future of Private Messaging
December 01, 2025 / Session
Removing screenshot alerts from Session
November 09, 2025 / Session
Session Pro Beta Development Update: Progress and Community Insights
October 30, 2025 / Session
Session Pro Beta: September Development Update
September 23, 2025 / Alex Linton