What happens if Twitter gets encrypted DMs?
May 06, 2022 / Alex LintonPrivacy, Private messaging
Welcome to yet another article discussing Elon Musk’s attempted acquisition of Twitter. It might seem like everyone has been weighing in on this recently, and that's because... they have been — including us, actually. This one isn't just about Elon, though — it's about something very close to our heart here at Session. Encryption. Ah, encryption. The lifeblood of cybersecurity.
So, Elon has been tweeting about Twitter a lot lately, and among the avalanche was this remark:
Okay...it's a bold claim, but what would this really change about the way Twitter works? Would it help users? Would it really be 'like Signal'?
Would end-to-end encrypted DMs be a good thing?
Yes — more encryption is good — obviously. We're strong advocates for encryption and encourage more platforms to embrace end-to-end encryption for the privacy and security of their users.
But — Twitter is still an open and non-private social media platform, and that involves a whole lot more than just its DM feature. In fact, DMs aren’t even really that commonly used on Twitter (compared to other social media apps like Facebook or Instagram) Having said that, using encryption is the absolute bare minimum that a platform can do to provide privacy and security.
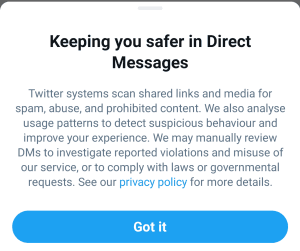
The addition of end-to-end encryption would still be really useful, especially with Twitter’s current policies allowing for employees to manually check user DMs for various reasons — late last year they were even rolling out in-app notifications reminding users about their ability to do so.
As far as social media platforms go, Twitter's design is more privacy-respecting than something like Facebook — it lets users stay pseudonymous, after all. But there is still a long way to go!
Can Twitter DMs really be 'like Signal'?
No. The idea that all Twitter would need to do to match Signal is add encryption is really, really underestimating how complex and sophisticated the Signal protocol is.
Even WhatsApp, who have a fully-fledged implementation of the Signal protocol, is still not really 'like Signal'. Why? Well, Signal a heap of goodwill built up from years of privacy-respecting behaviour, a team of developers updating and maintaining the protocol and the application to make sure it stays hardened to modern threats, and have set up their infrastructure to protect the privacy of their users (as much as a centralised service can, at least).
Twitter DMs are not—and can never be—the same. No matter what, at the very least Twitter DMs are very easily associated with your Twitter account — something which is completely public, has publicly observable behaviour, and can provide a huge amount of context and metadata which, in combination with (encrypted) messages, means your messages are still not really private — even if the contents are hidden.
As an analyst, I would prefer to be looking at metadata than looking at content, because it's quicker and easier, and it doesn't lie.
Edward Snowden, on the value of metadata
Messaging apps striving for privacy—like Signal—go to great lengths to minimise the amount of user metadata which is collected or exposed — and Twitter? Well, Twitter doesn't.
So what's the problem? Isn't this just a good thing?
Overall, we think that adding end-to-end encryption to Twitter DMs would be a good move. However, don't let anyone convince you that this means Twitter is private — Twitter still isn't private whether it has encrypted DMs or not. Often when discussing privacy and security—whether it be from the perspective of technologists, law enforcement agencies, or regulators—the conversation is disproportionately focused on encryption. As we've said many times before, encryption is just the first step — there are many, many more steps beyond that which are required to pass the privacy sniff test.
While we advocate for the use and implementation of strong encryption, we don't want to see encryption caught up in big tech's attempts at privacy washing.
In case you haven't already seen it, we also made a video about this topic! You can watch it right here:
Rotating keys for Session repos
January 22, 2026 / Session
Session Pro Beta update: December 2025
December 07, 2025 / Session
Session Protocol V2: PFS, Post-Quantum and the Future of Private Messaging
December 01, 2025 / Session
Removing screenshot alerts from Session
November 09, 2025 / Session
Session Pro Beta Development Update: Progress and Community Insights
October 30, 2025 / Session
Session Pro Beta: September Development Update
September 23, 2025 / Alex Linton